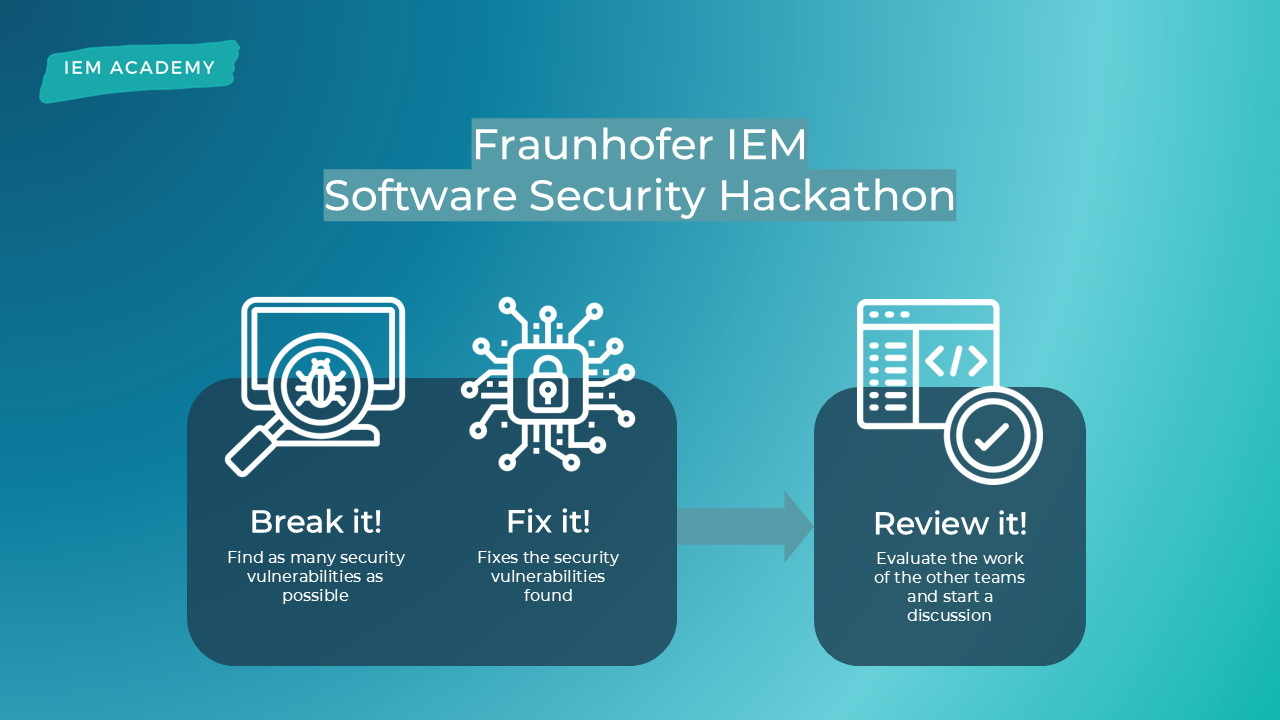
The threat posed by security vulnerabilities in software products is a growing danger to the success of companies of all sizes and in all industries. This makes it all the more important for software developers to have the necessary skills to secure their products and thus contribute to strengthening cyber resilience.
In our innovative hackathon ‘Break it, Fix it, Review it’, you will be challenged to demonstrate your software security skills in a team competition. In a practical setting, you will learn how to identify, evaluate and fix security vulnerabilities. You will also take on the role of reviewer and practise evaluating the work of your colleagues, before discussing it with them and developing secure solutions together.
This training is aimed at developers who already have basic knowledge of software security. Among other things, it provides an ideal transition between the Certified Security Champion Training and the everyday work of future security champions. It is also a suitable follow-up to our 2-day Software Security Training for Developers.
 Fraunhofer Institute for Mechatronic Systems Design
Fraunhofer Institute for Mechatronic Systems Design